Thu Feb 27 18:35:50 2020
<773ab1f1> In case you boys are curious, that position I’m going up for is helping a SEIM define ML-based detection
<773ab1f1> <https://www.youtube.com/watch?v=ce2F_FHE4xs&list=PL8BogY0hWwvyyrU-puszZ9K-lj1It6XTd> <—- this is an example of it
— Machine Learning for Security Analysts – Part 3: Malicious URL Predictor
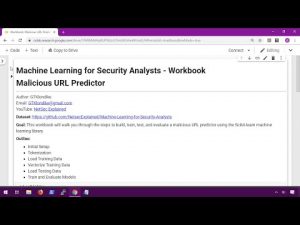
<773ab1f1> Couple that with something like this: <https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/windows-index.md> <—- boom. The answers to the test 😉
— atomics/windows-index.md
— “`
# Windows Atomic Tests by ATT&CK Tactic & Technique
# defense-evasion
– [T1134 Access Token Manipulation](./T1134/T1134.md)
– Atomic Test #1: Access Token Manipulation [windows]
– [T1197 BITS Jobs](./T1197/T1197.md)
– Atomic Test #1: Download & Execute [windows]
– Atomic Test #2: Download & Execute via PowerShell BITS [windows]
– Atomic Test #3: Persist, Download, & Execute [windows]
– [T1009 Binary Padding](./T1009/T1009.md)
– [T1088 Bypass User Account Control](./T1088/T1088.md)
– Atomic Test #1: Bypass UAC using Event Viewer [windows]
– Atomic Test #2: Bypass UAC using Event Viewer – PowerShell [windows]
– Atomic Test #3: Bypass UAC using Fodhelper [windows]
– Atomic Test #4: Bypass UAC using Fodhelper – PowerShell [windows]
– Atomic Test #5: Bypass UAC using ComputerDefaults – PowerShell [windows]
– Atomic Test #6: Bypass UAC by Mocking Trusted Directories [windows]
– [T1191 CMSTP](./T1191/T1191.md)
– Atomic Test #1: CMSTP Executing Remote Scriptlet [windows]
– Atomic Test #2: CMSTP Executing UAC Bypass [windows]
– T1116 Code Signing [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1500 Compile After Delivery](./T1500/T1500.md)
– Atomic Test #1: Compile After Delivery using csc.exe [windows]
– [T1223 Compiled HTML File](./T1223/T1223.md)
– Atomic Test #1: Compiled HTML Help Local Payload [windows]
– Atomic Test #2: Compiled HTML Help Remote Payload [windows]
– T1109 Component Firmware [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– T1122 Component Object Model Hijacking [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1090 Connection Proxy](./T1090/T1090.md)
– Atomic Test #2: portproxy reg key [windows]
– [T1196 Control Panel Items](./T1196/T1196.md)
– Atomic Test #1: Control Panel Items [windows]
– [T1207 DCShadow](./T1207/T1207.md)
– Atomic Test #1: DCShadow – Mimikatz [windows]
– [T1038 DLL Search Order Hijacking](./T1038/T1038.md)
– Atomic Test #1: DLL Search Order Hijacking – amsi.dll [windows]
– [T1073 DLL Side-Loading](./T1073/T1073.md)
– Atomic Test #1: DLL Side-Loading using the Notepad++ GUP.exe binary [windows]
– [T1140 Deobfuscate/Decode Files or Information](./T1140/T1140.md)
– Atomic Test #1: Deobfuscate/Decode Files Or Information [windows]
– Atomic Test #2: Certutil Rename and Decode [windows]
– [T1089 Disabling Security Tools](./T1089/T1089.md)
– Atomic Test #8: Unload Sysmon Filter Driver [windows]
– Atomic Test #9: Disable Windows IIS HTTP Logging [windows]
– Atomic Test #10: Uninstall Sysmon [windows]
– Atomic Test #11: AMSI Bypass – AMSI InitFailed [windows]
– Atomic Test #12: AMSI Bypass – Remove AMSI Provider Reg Key [windows]
– Atomic Test #13: Disable Arbitrary Security Windows Service [windows]
– Atomic Test #14: Disable PowerShell Script Block Logging [windows]
– Atomic Test #15: PowerShell Bypass of AntiMalware Scripting Interface [windows]
– Atomic Test #16: Tamper with Windows Defender ATP PowerShell [windows]
– Atomic Test #17: Tamper with Windows Defender Command Prompt [windows]
– Atomic Test #18: Tamper with Windows Defender Registry [windows]
– T1480 Execution Guardrails [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– T1211 Exploitation for Defense Evasion [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– T1181 Extra Window Memory Injection [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1107 File Deletion](./T1107/T1107.md)
– Atomic Test #4: Delete a single file – Windows cmd [windows]
– Atomic Test #5: Delete an entire folder – Windows cmd [windows]
– Atomic Test #6: Delete a single file – Windows PowerShell [windows]
– Atomic Test #7: Delete an entire folder – Windows PowerShell [windows]
– Atomic Test #8: Delete VSS – vssadmin [windows]
– Atomic Test #9: Delete VSS – wmic [windows]
– Atomic Test #10: bcdedit [windows]
– Atomic Test #11: wbadmin [windows]
– Atomic Test #13: Delete-PrefetchFile [windows]
– Atomic Test #14: Delete TeamViewer Log Files [windows, macos]
– T1006 File System Logical Offsets [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1222 File and Directory Permissions Modification](./T1222/T1222.md)
– Atomic Test #1: Take ownership using takeown utility [windows]
– Atomic Test #2: Take ownership recursively using takeown utility [windows]
– Atomic Test #3: cacls – Grant permission to specified user or group [windows]
– Atomic Test #4: cacls – Grant permission to specified user or group recursively [windows]
– Atomic Test #5: icacls – Grant permission to specified user or group [windows]
– Atomic Test #6: icacls – Grant permission to specified user or group recursively [windows]
– Atomic Test #7: attrib – Remove read-only attribute [windows]
– T1484 Group Policy Modification [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1158 Hidden Files and Directories](./T1158/T1158.md)
– Atomic Test #3: Create Windows System File with Attrib [windows]
– Atomic Test #4: Create Windows Hidden File with Attrib [windows]
– Atomic Test #8: Create ADS command prompt [windows]
– Atomic Test #9: Create ADS PowerShell [windows]
– [T1143 Hidden Window](./T1143/T1143.md)
– Atomic Test #1: Hidden Window [windows]
– [T1183 Image File Execution Options Injection](./T1183/T1183.md)
– Atomic Test #1: IFEO Add Debugger [windows]
– Atomic Test #2: IFEO Global Flags [windows]
– T1054 Indicator Blocking [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– T1066 Indicator Removal from Tools [CONTRIBUTE A TEST](<https://atomicredteam.io/contributing>)
– [T1070 Indicator Removal on Host](./T1070/T1070.md)
– Atomic Test #1: Clear Logs [windows]
– Atomic Test #2: FSUtil [windows]
– Atomic Test #6: Delete System Logs Using PowerShell [windows]
– Atomic Test #7: Delete System Logs Using Clear-EventLogId [windows]
– [T1202 Indirect Command Execution](./T1202/T1202.md)
– Atomic Test #1: Indirect Command Execution – pcalua.exe [windows]
– Atomic Test #2: Indirect Command Execution – forfiles.exe [windows]
– [T1130 Install Root Certificate](./T1130/T1130.md)
– [T1118 InstallUtil](./T1118/T1118.md)
– Atomic Test #1: InstallUtil uninstall method call [windows]
– Atomic Test #2: InstallUtil GetHelp method call [windows]
– [T1036 Masquerading](./T1036/T1036.md)
– Atomic Test #1: Masquerading as Windows LSASS process [windows]
– Atomic Test #3: Masquerading – cscript.exe running as notepad.exe [windows]
– Atomic Test #4: Masquerading – wscript.exe running as svchost.exe [windows]
– Atomic Test #5: Masquerading – powershell.exe running as taskhostw.exe [windows]
– Atomic Test #6: Masquerading – non-windows exe running as windows exe [windows]
– Atomic Test #7: Masquerading – windows exe running as different windows exe [windows]
– Atomic Test #8: Malicious process Masquerading as LSM.exe [windows]
– [T1112 Modify Registry](./T1112/T1112.md)
– Atomic Test #1: Modify Registry of Current User Profile – cmd [windows]
– Atomic Test #2: Modify Registry of Local Machine – cmd [windows]
– Atomic Test #3: Modify Registry of Another User Profile [windows]
– Atomic Test #4: Modify registry to store logon credentials [windows]
– Atomic Test #5: Modify registry to store PowerShell code [windows]
– Atomic Test #6: Add domain to Trusted sites Zone [windows]
– Atomic Test #7: Javascript in registry [windows]
– [T1170 Mshta](./T1170/T1170.md)
– Atomic Test #1: Mshta executes JavaScript Scheme Fetch Remote Payload With GetObject [windows]
– Atomic Test #2: Mshta calls a local VBScript file to launch notepad.exe [windows]
– Atomic Test #3: Mshta executes VBScript to execute malicious command [windows]
– Atomic Test #4: Mshta Executes Remote HTML Application (HTA) [windows]
– [T1096 NTFS File Attributes](./T1096/T1096.md)
– Atomic Test #1: Alternate Data Streams (ADS) [windows]
– Atomic Test #2: Store file in Alternate Data Stream (ADS)…